
Don’t Put All Your Eggs in One Basket – The 3-2-1 Backup Strategy Explained
 Remember Luke Skywalker setting out to destroy the Death Star with only one set of its plans stored in a little droid’s head? Losing them would likely have doomed his mission to save the galaxy. Similarly, in our digital world, safeguarding data is crucial. The 3-2-1 backup strategy is a vital defense against data loss. This article gives a basic overview of the 3-2-1 backup rule as well as explains advanced tactics that may be used to make data even more secure.
Remember Luke Skywalker setting out to destroy the Death Star with only one set of its plans stored in a little droid’s head? Losing them would likely have doomed his mission to save the galaxy. Similarly, in our digital world, safeguarding data is crucial. The 3-2-1 backup strategy is a vital defense against data loss. This article gives a basic overview of the 3-2-1 backup rule as well as explains advanced tactics that may be used to make data even more secure.
This is what you will learn in the next few minutes:
- What is the 3-2-1 backup strategy?
- Why is the 3-2-1 rule essential for data protection?
- How to implement the 3-2-1 backup method effectively?
- The role of off-site backup in the 3-2-1 strategy
- What is the 3-3-2-1-1 Rule, and how is it applied in its specific context?
What is a 3-2-1 Backup Strategy?
The 3-2-1 backup strategy is a foundational approach in data management and protection, widely advocated for its effectiveness in securing data against loss or corruption. The strategy’s name itself outlines its three core components: three copies of data, stored on two different forms of media, with one copy kept offsite.
The first component of the strategy involves creating three separate copies of your data. This means having the original set of data plus two backups. This triad of copies offers a robust safety net against data loss. For instance, if one backup fails or gets corrupted, there is still another backup available. The idea is to eliminate the single point of failure, which is a common risk in data storage and management.
The second and third components of the strategy focus on the method and location of storage. Storing data on two different types of media(e.g. Tape) or platforms reduces the risk of simultaneous loss due to a single type of failure. For example, you might have one copy on an internal hard drive and another on an external SSD or in cloud storage.
The last principle, keeping one backup offsite, is a guard against physical disasters like fire, flood, or theft that could destroy all local copies. Offsite storage can be as simple as a physical drive in a secure, remote location or as modern as cloud-based storage. This geographical diversification of data storage further solidifies the data protection strategy, making the 3-2-1 rule a gold standard in data backup and disaster recovery planning. You can request a demo of 3-2-1 Backup here.
A Sobering Picture Of Today’s Digital Landscape
On top of that, the 3-2-1 backup strategy is crucial in defending against rising hacker attacks. According to the research, there were 470 publicly disclosed security incidents in November 2023, involving 519,111,354 compromised records. The 3-2-1 backup strategy can largely reduce the risk of total data loss from cyber threats like ransomware.
“2023 has unveiled a stark reality in the digital realm: a surge of hacking groups exploiting vulnerabilities to launch attacks across numerous industries. Cybercrime, in all of its many forms, is here to stay. Too many organizations are making too much money for them to ever die. As we all know, ransomware and vulnerability incidents exemplify the daily threats that organizations face, leading to significant operational and financial repercussions,” said Ken Barth, CEO of Catalogic Software.
“These developments have made it clear that a comprehensive cybersecurity strategy is no longer optional but essential. As the market evolves, we are seeing more and more creativity as the attackers gain experience on how best to penetrate their targets,” he added.
Piecing Together Your 3-2-1 Backup Strategy
The 3-2-1 backup strategy is widely regarded as a standard in the realm of information security and data preservation. While this method doesn’t completely eliminate the possibility of data compromise, it significantly reduces the risks associated with backup procedures.
Here’s how data recovery works under the 3-2-1 approach:
- If the primary (active) data is corrupted, damaged, or lost, the first step is to retrieve the data from an in-house backup stored on a different medium or secondary storage system.
- Should the second data copy be inaccessible or compromised, the focus shifts to the off-site backup, which is then restored to the internal servers.
- After successfully restoring data, it’s crucial to restart the 3-2-1 backup process immediately. This ensures continuous and effective protection of the data.
A Step Beyond the 3-2-1 Backup Strategy
The 3-2-1 backup strategy has proven effective over time as a data protection method. However, with the evolution of storage systems and services, certain aspects of this strategy may need adaptation to fulfill current data protection goals.
Managing the multiple data copies in a 3-2-1 backup framework can become complex, depending on the backup methods an organization employs within this strategy.
Moreover, many organizations find themselves customizing their backup policies further while still maintaining the core principles of the 3-2-1 strategy. This leads to a modified approach, often referred to as the 3-2-1-#-#-# rule.
Introducing Catalogic Software
Catalogic Software stands as a bastion in the realm of data protection and bare metal restoration. Functioning as a crucial layer in the cybersecurity ecosystem of their customers, Catalogic supplements existing endpoint solutions and feeds data into their SIEM systems. They recognize that data protection, including bare metal restoration capabilities, is a customer’s last line of defense against various causes of outages.
With three decades of expertise in data protection, Catalogic is incessantly working to counteract escalating cyber threats. Our flagship product, DPX, delivers a secure data protection solution with instant recoverability to help ensure you can protect your backup data set from ransomware and recover data in an instant when you need it. With DPX, you have integrated ransomware protection.
- Support for the 3-2-1-1 rule that provides a robust data protection solution with verified scheduled recoveries for automated recovery testing,
- 3 copies of your data,
- 2 copies stored on different storage media types,
- 1 of the copies offsite or in the cloud(Azure, AWS, Wasabi, Backblaze B2, etc, you name it) on immutable media,
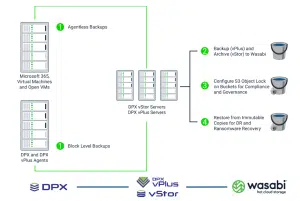
- 1 copy verified as recoverable.
Catalogic’s Variation: the 3-3-2-1-1 Rule
The 3-3-2-1-1 data protection rule offers a comprehensive approach to safeguarding data. Firstly, it emphasizes maintaining at least three copies of your data. Unique to this strategy, three of these copies are pre-scanned by GuardMode, adding an extra layer of ransomware protection. GuardMode actively monitors for suspicious activity, promptly alerts users, and prevents ransomware from encrypting backups.
Additionally, it’s advisable to keep these copies on two different types of media, enhancing data security by diversifying storage formats. Storing at least one copy in an off-site location, preferably air-gapped, further secures the data against local disasters or network breaches.
Finally, the rule includes maintaining one verified copy, specifically for recovery purposes, ensuring data integrity and swift restoration in case of data loss. This approach effectively blends traditional backup strategies with advanced, proactive security measures.
Closing Thoughts
Data is invaluable, and the 3-2-1 backup strategy is a key defense against data loss from cyberattacks, natural disasters, or human error. As a fundamental step in establishing a solid data backup policy, Catalogic collaborates with organizations to tailor backup solutions, accommodating any number of backups, choice of media, and storage locations, whether on-premises or in the cloud.
May the backups be with you always!

