Selecting the right virtualization platform is a critical decision for IT departments aiming to boost efficiency, reduce costs, and scale operations effectively. With VMware and Proxmox VE leading the pack, each platform offers distinct advantages. Proxmox VE, with its open-source framework, is particularly appealing for its cost-effectiveness and flexibility. This contrasts VMware, a proprietary solution known for its comprehensive support and scalability, though often at a higher cost. Recent changes in VMware’s licensing, influenced by corporate decisions, have led some organizations to consider Proxmox VE as a more customizable and financially accessible option.
The Critical Role of Backup in Migration
Migrating from VMware to Proxmox VE necessitates a strategic approach, with data backup being a cornerstone of the transition. It’s crucial to maintain backups both before and after the migration for both virtualization platforms. Additionally, it’s necessary to retain backup data for a period, as VM administrators need to run test systems to ensure everything operates smoothly. This process highlights the differences in backup methodologies between VMware and Proxmox VE, each tailored to its respective platform’s architecture.
VMware Backup vs. Proxmox VE Backup
For VMware environments, usually the backup software adopts an agentless approach, streamlining the backup process by eliminating the need for installing backup agents on each VM. This method leverages VMware vCenter and a virtualization proxy server to manage VMware snapshot processing and communication with the storage destination. It enables auto-discovery and protection of new or modified VMs, ensuring comprehensive coverage. Additionally, the backup software offers instant recovery options, including the ability to quickly map Virtual Machine Disk (VMDK) images back to the same or alternate VMs, significantly reducing downtime and enhancing data accessibility. The support for both physical and virtual environments underlines the backup solution’s versatility, catering to a wide range of backup and recovery needs.
In contrast, the approach for Proxmox backup with backup software is similarly agentless but specifically tailored to the Proxmox VE platform. It incorporates hypervisor snapshot management, enabling efficient backup and recovery processes. One of the features for Proxmox VE backups allows for incremental backups after an initial full backup, focusing only on changed data to minimize backup windows and storage requirements. Backup software also provides a disk-exclusion option, enabling users to exclude certain VM disks from backups. This can be particularly advantageous for optimizing backup storage by omitting disks that contain temporary or non-essential data.
The distinction between VMware and Proxmox backup strategies illustrates the tailored functionalities that backup software must provide to effectively cater to each platform. VMware’s solution emphasizes comprehensive coverage, instant recovery, and streamlined integration within a diverse and complex IT infrastructure. Meanwhile, Proxmox’s backup solution focuses on efficiency, flexibility, and the specific virtualization technologies of Proxmox VE, offering scalable and efficient data protection. This highlights the critical role of choosing a backup solution that not only matches the technical framework of the virtualization environment but also supports the strategic goals of the organization’s data protection policies.











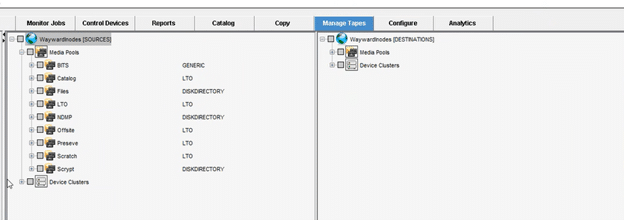 The tape migration process can also be helpful for moving media types of type DISKDIRECTORY
The tape migration process can also be helpful for moving media types of type DISKDIRECTORY