A regular backup upgrade is crucial for cybersecurity. Yet, many overlook the importance of updating backup software. It’s a critical step. Why is it so vital? Backup software acts as your final safeguard against data loss and corruption. If cyber threats compromise your systems, robust backup software is key. It enables swift recovery. This minimizes the damage. Make sure to prioritize your backup software upgrade. It’s an essential defense in your digital environment.
8 Reasons to Prioritize Your Backup Software Upgrade
Upgrading backup software is paramount for organizations striving to enhance their cyber resilience. Upgrading backup software is of utmost importance for organizations aiming to improve their cyber resilience. This is because backup software plays a critical role in the overall data protection and recovery strategy of an organization. By upgrading their backup software, organizations can benefit from several key advantages:
1. Advanced Security Features.
Newer versions of backup software often come with improved security features, such as enhanced encryption algorithms, stronger authentication mechanisms, and better access controls. These features help protect backup data from unauthorized access and ensure its integrity.
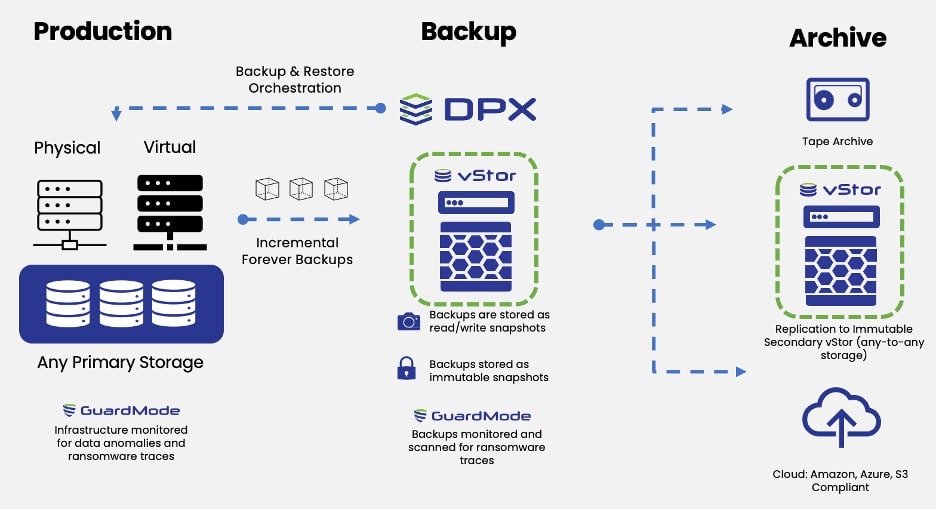
For DPX users, features like GuardMode, vStor, and revamped user interfaces can bolster an organization’s ability to protect and recover data in the face of evolving cyber threats.
2. Better Compatibility.
As technology evolves, older backup software may become incompatible with newer operating systems, hardware, and applications. Upgrading to the latest version ensures compatibility with the latest IT infrastructure, allowing organizations to seamlessly protect and recover their data.
3. Increased Performance.
Upgraded backup software often includes performance improvements like faster backup and recovery speeds, optimized resource utilization, and better handling of large data sets. These enhancements reduce downtime and improve overall operational efficiency.
4. Enhanced Automation and Integration.
Modern backup software offers increased automation capabilities and integration with other IT systems, enabling organizations to streamline their backup processes. Automation reduces the chances of human error, ensures regular backups, and simplifies disaster recovery workflows.
5. Advanced Recovery Options.
Upgraded backup software may introduce new recovery options, such as instant VM recovery, granular item-level recovery, and cross-platform recovery. These options grant organizations more flexibility and efficiency when restoring data after a cyber incident.
6. Better Data Management:
Upgraded backup software often includes advanced data management features like deduplication, compression, and tiered storage. These features help optimize storage utilization and reduce costs, making backup operations more efficient and cost-effective.
7. Compliance and Regulation
Many industries have specific data protection regulations that organizations must adhere to. Up-to-date backup software often includes features that help organizations meet these regulatory requirements, such as data retention policies, audit logs, and reporting capabilities.
8. Pro-Bono Upgrade Services
The availability of pro-bono upgrade services from software providers can be a game-changer. This offering not only ensures that organizations stay current with the latest security enhancements but also demonstrates a commitment to cybersecurity from the software vendor’s side, forging a stronger partnership in the battle against data breaches and cyberattacks.
In conclusion, upgrading backup software ensures the security, compatibility, performance, automation, recovery options, data management, and compliance necessary to effectively protect data and withstand cyber threats. Several key factors drive the urgency of this endeavor.
Checking Compatibility Before Backup Upgrades
Assessing the compatibility of the latest backup software version with an organization’s existing infrastructure is a critical step in the decision-making process for upgrades. To ensure a seamless transition, several considerations come into play.
The assurance of two-version backward compatibility provides peace of mind by ensuring that the new software can work with data from the current and previous two versions, safeguarding data integrity during the upgrade process.
The choice between agent-based and agentless backups must align with the specific requirements and constraints of the infrastructure.
Additionally, the availability of a compatibility matrix published by the software provider simplifies the evaluation process, offering a clear roadmap for compatibility checks.
Furthermore, the ability to upgrade the master server independently, taking advantage of the latest feature sets, while scheduling upgrades for agent nodes at a later time, allows for a phased approach that minimizes disruptions.
Lastly, the inclusion of an inventory and version report directly within the user interface streamlines the assessment, providing a real-time snapshot of compatibility and ensuring informed decisions that bolster the organization’s cyber resilience.
Simplified Backup Management in New DPX Update
Usability Enhancements in DPX’s Latest Release
The latest version of DPX has brought several significant improvements from a usability standpoint, greatly enhancing day-to-day backup administration tasks.
One of the most noticeable enhancements has been the transition to a more user-friendly WebUI and simplified management interface. The latest DPX has made it much more intuitive and accessible, allowing administrators to efficiently manage their backup infrastructure with ease.
GuardMode: Advancing Event Monitoring in DPX
Event monitoring has also seen remarkable improvements, particularly with the introduction of features like GuardMode. This cyber-resilient approach ensures that critical data remains vigilant even in the face of potential threats. The ability to monitor events in real-time and proactively respond to potential security breaches has become an integral part of backup administration, bolstering cybersecurity efforts.
Transparent Reporting: SLA and Chargeback in DPX
SLA-based reporting and chargeback mechanisms have made tracking storage usage and data growth more transparent and actionable. Administrators can now generate reports that provide valuable insights into storage consumption trends, enabling better resource allocation and cost management. This level of visibility into the backup environment empowers organizations to optimize their backup strategies.
Improved Security with DPX’s Role-Based Access Control
Furthermore, the latest DPX version has introduced improved role-based access control, allowing for more granular control over who can access and modify backup configurations. This feature enhances security and ensures that only authorized personnel can make critical changes, reducing the risk of accidental data loss or configuration errors.
vStor Management: User Interface Improvements in DPX
The management of vStor, a key component of the backup infrastructure, has also seen notable enhancements in terms of its user interface (UI). The improved UI simplifies the process of managing storage resources, making it more efficient and user-friendly.
For DPX users, you can watch this YouTube video to check out “How to Migrate Your DPX Windows Master Server Seamlessly”.
Takeaway: Why Upgrading Your Backup Software is Essential
Upgrading your backup software should be a non-negotiable part of your cybersecurity strategy. It’s not just about staying current; it’s about ensuring your organization’s survival in the face of cyber threats. Here’s why:
- Minimize Disruption: VM software-based solutions offer an easy upgrade path, often with little to no downtime, so you can continue to protect your data seamlessly.
- Leverage New Features: With DPX’s GuardMode, vStor, and improved interfaces, you’re better equipped to fend off and recover from cyber incidents.
- Benefit from Free Services: Many providers, like those of DPX, offer pro-bono upgrades, highlighting their commitment to your cybersecurity and offering a partnership in defense against data breaches.
- Ensure Compatibility: Always check that new backup software aligns with your existing systems to guarantee a smooth transition and maintain data integrity.
- Enhanced Usability: The new DPX version’s user-friendly interface and management features simplify backup administration, allowing you to manage backups more effectively and securely.
Remember, neglecting your backup software upgrades is a risk you can’t afford. Stay ahead of the curve and ensure your last line of defense is as strong as it can be.