Tape vs Cloud: Smart Backup Choices with LTO Tape for Your Business
In an era dominated by digital transformations and cloud-based solutions, the choice between LTO backup and cloud storage remains a critical decision for businesses. While cloud storage offers scalability and accessibility, tape backup systems, particularly with modern LTO technologies, provide unmatched cost efficiency, longevity, and air-gapped security. But how do you decide which option aligns best with your business needs? Let’s explore the tape vs cloud debate and find the right backup tier for your organization.
Understanding LTO Backup and Its Advantages
Linear Tape-Open (LTO) technology has come a long way since its inception. With the latest LTO-9 tapes offering up to 18TB of native storage (45TB compressed), the sheer capacity makes LTO backup a cost-effective choice for businesses handling massive data volumes.
Key Benefits of LTO Backup:
- Cost Efficiency: Tape storage remains one of the cheapest options per terabyte, especially for long-term archiving.
- Air-Gapped Security: Unlike cloud storage, tapes are not continuously connected to a network, providing a physical air-gap against ransomware attacks.
- Longevity: Properly stored tapes can last over 30 years, making them ideal for long-term compliance or archival needs.
- High Throughput: Modern tape drives offer fast read/write speeds, often surpassing traditional hard drives in sustained data transfer.
However, while tape backup excels in cost and security, it comes with challenges such as limited accessibility, physical storage management, and the need for compatible hardware.
The Case for Cloud Storage
Cloud storage solutions have surged in popularity, driven by their flexibility, accessibility, and seamless integration with modern workflows. Services like Amazon S3 Glacier and Microsoft Azure Archive offer cost-effective options for storing less frequently accessed data.
Why Cloud Storage Works:
- Accessibility and Scalability: Cloud storage allows instant access to data from anywhere and scales dynamically with your business needs.
- Automation and Integration: Backups can be automated, and cloud APIs integrate effortlessly with other software solutions.
- Reduced On-Premise Overhead: No need for physical infrastructure or manual tape swaps.
- Global Redundancy: Cloud providers often replicate your data across multiple locations, ensuring high availability.
However, cloud storage also comes with risks like potential data breaches, ongoing subscription costs, and dependency on internet connectivity.
Tape vs Cloud: A Side-by-Side Comparison
| Feature | LTO Tape Backup | Cloud Storage |
| Cost Per TB | Lower for large data volumes | Higher, with ongoing fees |
| Accessibility | Limited, requires physical access | Instant, from any location |
| Longevity | 30+ years if stored correctly | Dependent on subscription and provider stability |
| Security | Air-gapped, immune to ransomware | Prone to cyberattacks |
| Scalability | Limited by physical storage | Virtually unlimited |
| Speed | High sustained transfer rates | Dependent on internet bandwidth |
| Environmental Impact | Low energy during storage | Energy-intensive due to data centers |
Choosing the Right Backup Tier for Your Business
When deciding between tape vs. cloud, consider your specific business requirements:
- Long-Term Archival Needs: If your business requires cost-effective, long-term storage with low retrieval frequency, LTO backup is an excellent choice.
- Rapid Recovery and Accessibility: For data requiring frequent access or quick disaster recovery, cloud storage is more practical.
- Hybrid Approach: Many organizations adopt a hybrid strategy, using tapes for long-term archival and cloud for operational backups and disaster recovery.
The Rise of Hybrid Backup Solutions
As data management becomes increasingly complex, hybrid solutions combining LTO backup and cloud storage are gaining traction. This approach provides the best of both worlds: cost-effective, secure long-term storage through tapes and flexible, accessible short-term storage in the cloud.
For instance:
- Use LTO tape backup to store archival data that must be retained for compliance or regulatory purposes.
- Utilize cloud storage for active project files, frequent backups, and disaster recovery plans.
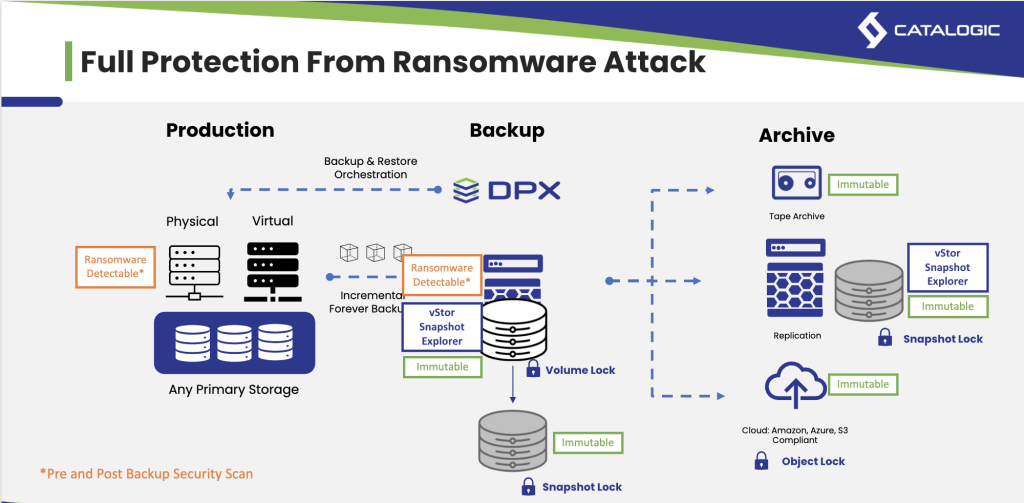
Trusted Solutions for Backup: Catalogic DPX
For over 25 years, Catalogic DPX has been a reliable partner for businesses navigating the complexities of data backup. With robust support for both tape backup and cloud backup, Catalogic DPX helps organizations implement effective, secure, and cost-efficient backup strategies. Its advanced features and intuitive management tools make it a trusted choice for businesses seeking to balance traditional and modern storage solutions.
Final Thoughts on Tape vs Cloud
Both LTO backup and cloud storage have unique strengths, making them suitable for different use cases. The tape vs. cloud decision should align with your budget, data accessibility needs, and risk tolerance. For organizations prioritizing cost efficiency and security, tape backup remains a compelling choice. Conversely, businesses seeking flexibility and scalability may prefer cloud storage.
Ultimately, a well-designed backup strategy often combines both, ensuring your data is secure, accessible, and cost-effective. As technology evolves, keeping an eye on advancements in both tapes and cloud storage will help future-proof your data management strategy.
By balancing the benefits of LTO tape backup and cloud storage, businesses can safeguard their data while optimizing costs and operational efficiency.