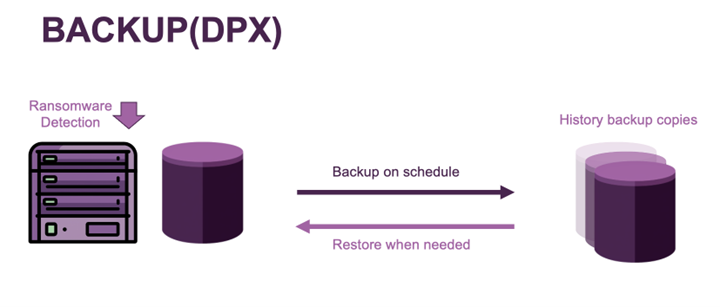
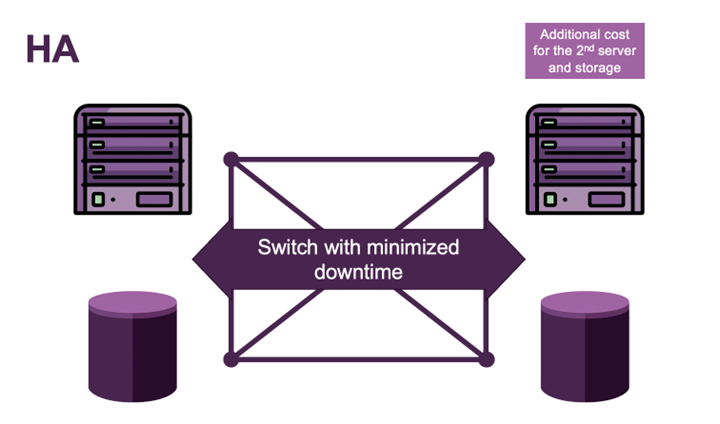
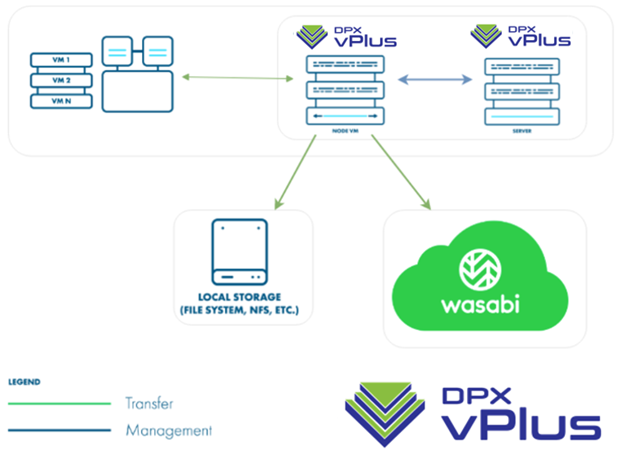
NDMPs Backup & Wiederherstellung – Die Top 11 Herausforderungen
Dateiebene NAS NDMP Wiederherstellungen: Ihr Alptraum oder unser gelöstes Problem?
Wenn kostenintensive Lizenzen, endlose Schulungssitzungen und träge, unzuverlässige Wiederherstellungen Ihre NAS NDMP Realität definieren, sind Sie nicht allein. Tauchen wir ein in die Herausforderungen der Datei-Wiederherstellung, die Speicheradministratoren plagen, und entfesseln die Kraft von Catalogic DPX als Ihren ultimativen Datenwiederherstellungshelden. Vergessen Sie Komplexität und Ausfallzeiten. DPX reduziert Kosten mit transparenter Preisgestaltung, vereinfacht Abläufe durch Automatisierung und liefert konstante Leistung mit einer benutzerfreundlichen Schnittstelle. Wir sprechen von effizienten Backups, solider Sicherheit und robustem Reporting – alles ohne die Bank zu sprengen. Also lassen Sie das Drama der Datenwiederherstellung hinter sich und erkunden Sie 11 Wege, wie Catalogic DPX Ihre Wiederherstellungsprobleme in Triumphe verwandelt.
-
Komplexe Lizenzierungsmodelle:
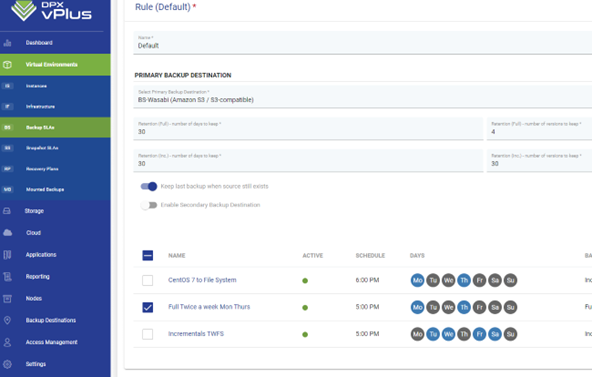
Einige Lösungen haben komplexe und verworrene Lizenzierungsmodelle, was es für Administratoren schwierig macht, Kosten effektiv zu verstehen und zu verwalten.
Catalogic DPX vereinfacht die Lizenzierung mit transparenten und unkomplizierten Modellen, die es Administratoren ermöglichen, Kosten effektiv und einfach zu verwalten.
-
Ungenügende Benutzeroberfläche:
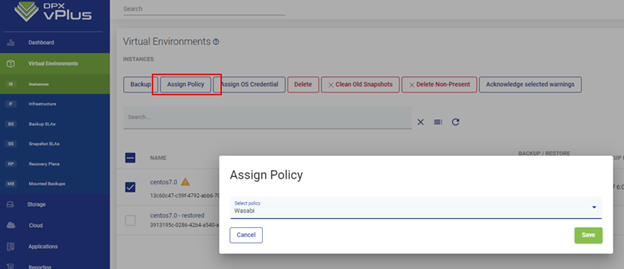
Schlecht gestaltete Benutzeroberflächen können die Effizienz von Administratoren beim Navigieren und Nutzen von Datei-Wiederherstellungsfunktionen behindern und so zu Verzögerungen bei der Datenwiederherstellung führen. Einige Oberflächen ohne Suchfunktionen machen die Datei-Wiederherstellungsfunktion praktisch nutzlos.
Catalogic DPX bietet eine gut gestaltete Benutzeroberfläche, die die Effizienz von Administratoren beim Navigieren, Suchen und Nutzen von Dateiebenen-Wiederherstellungsfunktionen erhöht und ein reibungsloses Erlebnis sicherstellt.
-
Verlängerte Ausfallzeiten:
Die Komplexitäten und Ineffizienzen bei Datei-Wiederherstellungsprozessen tragen zu verlängerten Ausfallzeiten bei, was sich negativ auf Geschäftsbetrieb und Produktivität der Benutzer auswirkt.
Catalogic DPX: Effiziente Datei-Wiederherstellungen in DPX tragen zu reduzierten Ausfallzeiten bei, die sich positiv auf Geschäftsbetrieb und Benutzerproduktivität auswirken.
-
Erhöhtes Risiko von Datenverlust:
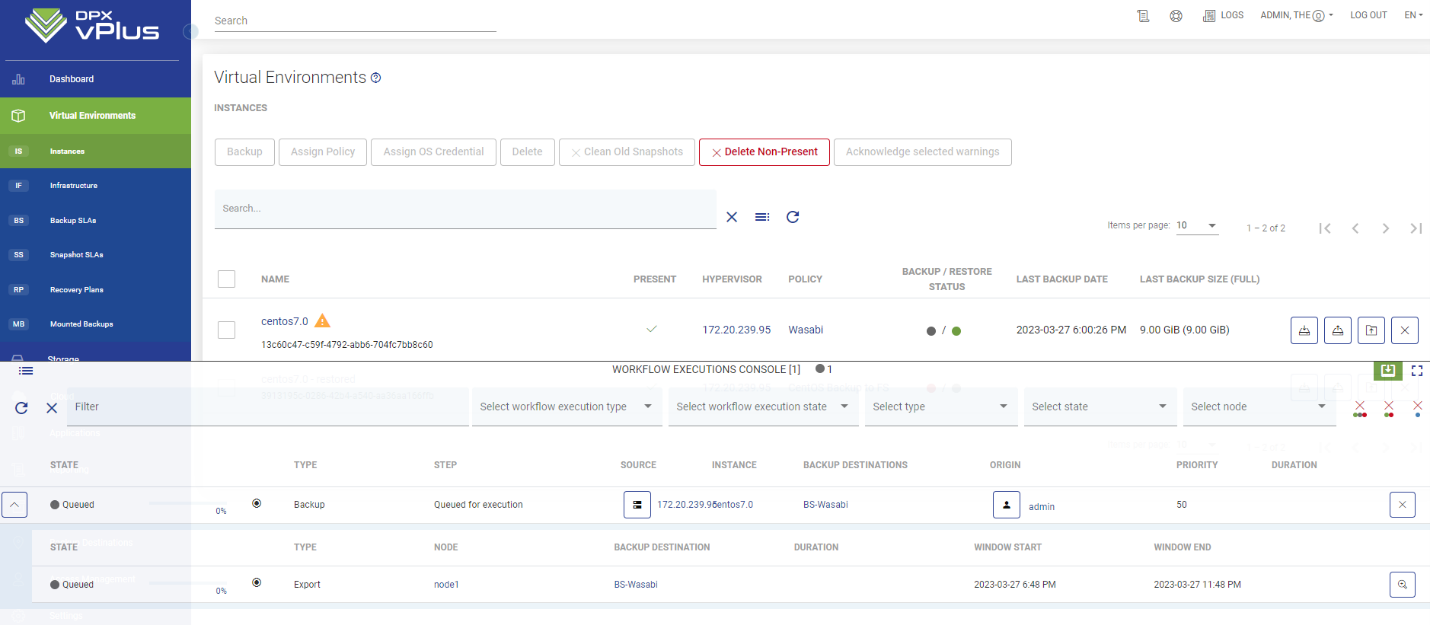
Umständliche Verfahren und mögliche Fehler bei Datei-Wiederherstellungen erhöhen das Risiko von Datenverlust und stellen eine erhebliche Bedrohung für die kritischen Informationen der Organisation dar.
Catalogic DPX: Die optimierten Prozesse in DPX minimieren das Risiko von Fehlern bei Datei-Wiederherstellungen, verbessern die Datenwiederherstellung und reduzieren die Bedrohung durch Datenverlust.
-
Ressourcenüberlastung:
Administratoren, die übermäßig viel Zeit mit manuellen Aufgaben und Fehlerbehebung bei Datei-Wiederherstellungsproblemen verbringen, lenken Ressourcen von anderen wichtigen IT-Verantwortlichkeiten ab.
Catalogic DPX minimiert manuelle Aufgaben und Fehlerbehebungsaufwand, reduziert die Ressourcenbelastung und ermöglicht es Administratoren, sich auf wichtige IT-Verantwortlichkeiten zu konzentrieren.
-
Höhere Gesamtbetriebskosten (TCO):
Die Kombination aus hohen Lizenzkosten, Schulungsausgaben und erhöhten Ausfallzeiten führt zu höheren Gesamtbetriebskosten für bestehende Lösungen.
Catalogic DPX: Mit wettbewerbsfähigen Preisen, optimierten Prozessen und reduzierten Ausfallzeiten trägt DPX zu niedrigeren Gesamtbetriebskosten im Vergleich zu bestehenden Lösungen bei.
-
Negative Auswirkungen auf die Benutzererfahrung:
Langsame Datei-Wiederherstellungsprozesse wirken sich negativ auf die Benutzererfahrung aus und führen zu Frustration bei Mitarbeitern und potenzieller Unzufriedenheit mit IT-Dienstleistungen.
Catalogic DPX: Verbesserte Effizienz bei Datei-Wiederherstellungen wirkt sich positiv auf die Benutzererfahrung aus, reduziert die Frustration der Mitarbeiter und erhöht die Zufriedenheit mit IT-Dienstleistungen.
-
Verpasste Wiederherstellungszeitziele (RTOs):
Ineffiziente Datei-Wiederherstellungen können dazu führen, dass RTOs verpasst werden, was die Fähigkeit der Organisation beeinträchtigt, Wiederherstellungsverpflichtungen einzuhalten.
Die optimierten Datei-Wiederherstellungsprozesse von Catalogic DPX tragen dazu bei, RTOs konsequent einzuhalten und rechtzeitig Wiederherstellungsverpflichtungen zu erfüllen.
-
Verminderte IT-Agilität:
Umständliche Prozesse und Einschränkungen in der Funktionalität von Datei-Wiederherstellungen behindern die IT-Agilität und erschweren eine schnelle Anpassung an sich ändernde Geschäftsanforderungen.
Die optimierten Prozesse und verbesserte Funktionalität von Catalogic DPX in DPX fördern die IT-Agilität und ermöglichen es Organisationen, sich schnell an sich ändernde Geschäftsanforderungen anzupassen.
-
Kompromittierte Datensicherheit:
Verlängerte Ausfallzeiten und potenzieller Datenverlust aufgrund von Herausforderungen bei Datei-Wiederherstellungen gefährden die Gesamtsicherheit sensibler Informationen.
Die zuverlässigen und effizienten Datei-Wiederherstellungsprozesse von Catalogic DPX tragen zur Aufrechterhaltung der Gesamtsicherheit sensibler Informationen während der Datenwiederherstellung bei.
-
Hohe Kosten:
Viele führende Softwarelösungen, die Datei-Wiederherstellung für NAS NDMP-Daten anbieten, sind mit hohen Lizenzkosten verbunden und somit finanziell belastend für Organisationen mit Budgetbeschränkungen.
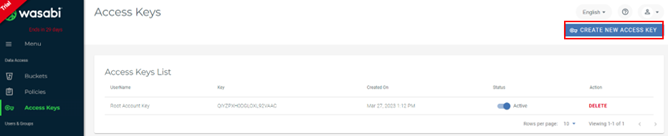
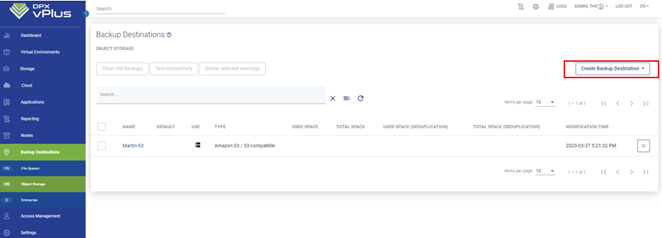
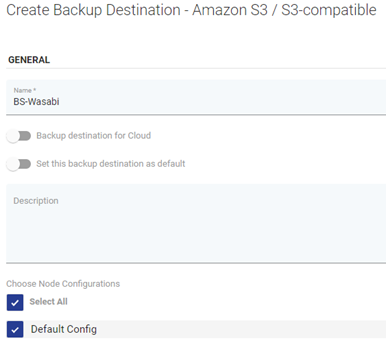
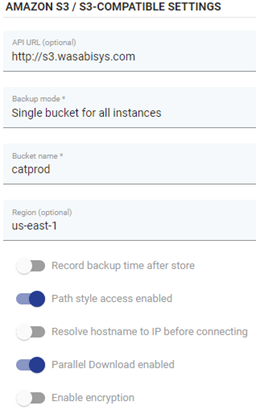
Catalogic DPX bietet wettbewerbsfähige Preise ohne Kompromisse bei robusten Funktionen und stellt so eine erschwingliche Option für Organisationen mit Budgetbeschränkungen dar. Erfahren Sie mehr über die DPX-Lösung von Catalogic, indem Sie hier klicken.