Catalogic vStor A Modern Software-Defined Backup Storage Platform
Here at Catalogic we can’t stress enough that having solid backups isn’t just important -it’s essential. But what happens when the backups themselves become targets? We’ve built a modern storage solution to address exactly that concern. That means that DPX customers are in a particularly fortunate position. Rather than having to shop around for a compatible backup storage solution, they get vStor included right in the DPX suite. This means they automatically benefit from enterprise-grade features like data deduplication, compression, and most importantly, robust immutability controls that can lock backups against unauthorized changes.
By combining DPX’s backup capabilities with vStor’s secure storage foundation, organizations gain a complete protection system that doesn’t require proprietary hardware or complex integration work. It’s a practical, cost-effective approach to ensuring your business data remains safe and recoverable, no matter what threats emerge.
Intro
This article will guide you through features and benefits of using vStor. For a lot of our customers it’s a refresher but might also be a good reminder to make sure you’re using the latest and greatest and most importantly – all the benefits that this solution is offering. Let’s start!
Catalogic vStor is a software-defined storage appliance designed primarily as a backup repository for Catalogic’s DPX data protection software. It runs on commodity hardware (physical or virtual) and leverages the ZFS file system to provide enterprise features like inline deduplication, compression, and replication on standard servers. This approach creates a cost-effective yet resilient repository that frees organizations from proprietary backup appliances and vendor lock-in.
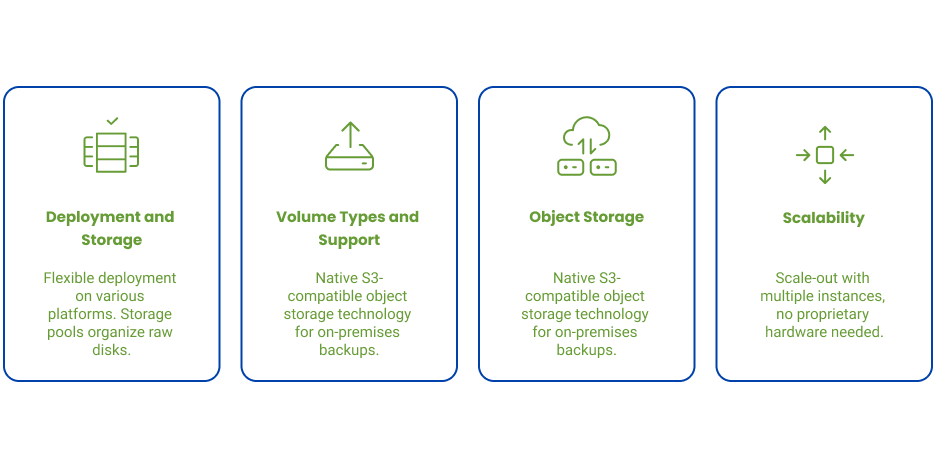
Storage Capabilities
Flexible Deployment and Storage Pools: vStor runs on various platforms (VMware, Hyper-V, physical servers) and uses storage pools to organize raw disks. Administrators can aggregate multiple disks (DAS, SAN LUNs) into expandable pools that grow with data needs. As a software-defined solution, vStor works with any block device without proprietary restrictions.
Volume Types and Protocol Support: vStor offers versatile volume types including block devices exported as iSCSI LUNs (ideal for incremental-forever backups) and file-based storage supporting NFS and SMB protocols (commonly used for agentless VM backups). The system supports multiple network interfaces and multipathing for high availability in SAN environments.
Object Storage: A standout feature in vStor 4.12 is native S3-compatible object storage technology. Each appliance includes an object storage server allowing administrators to create S3-compatible volumes with their own access/secret keys and web console. This enables organizations to keep backups on-premises in an S3-compatible repository rather than sending them immediately to public cloud. The object storage functionality supports features like Object Lock for immutability.
Scalability: Being software-defined, vStor can scale-out with multiple instances rather than being limited to a single appliance. Organizations can deploy nodes across different sites with varying specifications based on local needs. There’s no proprietary hardware requirement—any server with adequate resources can become a vStor node, contrasting with traditional purpose-built backup appliances.
Data Protection and Recovery
Backup Snapshots and Incremental Forever: vStor leverages ZFS snapshot technology to take point-in-time images of backup volumes without consuming full duplicates of data. Each backup is preserved as an immutable snapshot containing only changed blocks, aligning with incremental-forever strategies. Using Catalogic’s Snapshot Explorer or mounting volume snapshots, administrators can directly access backup content to verify data or extract files without affecting the backup chain.
Volume Replication and Disaster Recovery: vStor provides point-to-point replication between appliances for disaster recovery and remote office backup consolidation. Using partnerships, volumes on one vStor can be replicated to another. Replication is typically asynchronous and snapshot-based, transferring only changed data to minimize bandwidth. vStor 4.12 introduces replication groups to simplify managing multiple volume replications as a cohesive unit.
Recovery Features: Since backups are captured as snapshots, recoveries can be performed in-place or by presenting backup data to production systems. Instant Access recovery allows mounting a backup volume directly to a host via iSCSI or NFS, enabling immediate access to backed-up data or even booting virtual machines directly from backups—significantly reducing downtime. Catalogic DPX offers Rapid Return to Production (RRP) leveraging snapshot capabilities to transition mounted backups into permanent recoveries with minimal data copying.
Security and Compliance
User Access Control and Multi-Tenancy: vStor implements role-based access with Admin and Standard user roles. Standard users can be limited to specific storage pools, enabling multi-tenant scenarios where departments share a vStor but can’t access each other’s backup volumes. Management actions require authentication, and multi-factor authentication (MFA) is supported for additional security.
Data Encryption: vStor 4.12 supports volume encryption for data confidentiality. When creating a volume, administrators can enable encryption for all data written to disk. For operational convenience, vStor provides an auto-unlock mechanism via an “Encryption URL” setting, retrieving encryption keys from a remote secure server accessible via SSH. Management traffic uses HTTPS, and replication between vStors can be secured and compressed.
Immutability and Deletion Protection: One standout security feature is data immutability control. Snapshots and volumes can be locked against deletion or modification for defined retention periods—crucial for ransomware defense. vStor offers two immutability modes: Flexible Protection (requiring MFA to unlock) and Fixed Protection (WORM-like locks that cannot be lifted until the specified time expires). These controls help meet compliance standards and improve resilience against malicious attacks.
Ransomware Detection (GuardMode): vStor 4.12 introduces GuardMode Scan, which examines backup snapshots for signs of ransomware infection. Administrators can run on-demand scans on mounted snapshots or enable automatic scanning of new snapshots. If encryption patterns or ransomware footprints are detected, the system alerts administrators, turning vStor from passive storage into an active cybersecurity component.
Performance and Efficiency Optimizations
Inline Deduplication: vStor leverages ZFS deduplication to eliminate duplicate blocks and save storage space. This is particularly effective for backup data with high redundancy (e.g., VMs with identical OS files). Typical deduplication ratios range from 2:1 to 4:1 depending on data type, with some scenarios achieving 7:1 when combined with compression. vStor applies deduplication inline as data is ingested and provides controls to manage resource usage.
Compression: Complementary to deduplication, vStor enables compression on all data written to the pool. Depending on data type, compression can reduce size by 1.5:1 to 3:1. The combination of deduplication and compression significantly reduces the effective cost per terabyte of backup storage—critical for large retention policies.
Performance Tuning: vStor inherits ZFS tuning capabilities for optimizing both write and read performance. Administrators can configure SSDs as write log devices (ZIL) and read caches (L2ARC) to boost performance for operations like instant recovery. vStor allows adding such devices to pool configurations to enhance I/O throughput and reduce latency.
Network Optimizations: vStor provides network optimization options including bandwidth throttling for replication and compression of replication streams. Organizations can dedicate different network interfaces to specific traffic types (management, backup, replication). With proper hardware (SSD caching, adequate CPU), vStor can rival traditional backup appliances in throughput without proprietary limitations.
Integration and Automation
DPX Integration: vStor integrates seamlessly with Catalogic DPX backup software. In the DPX console, administrators can define backup targets corresponding to vStor volumes (iSCSI or S3). DPX then handles writing backup data and tracking it in the catalog. vStor’s embedded MinIO makes it possible to have an on-premises S3 target for DPX backups, achieving cloud-like storage locally.
Third-Party Integration: While optimized for DPX, vStor’s standard protocols (iSCSI, NFS, SMB, S3) enable integration with other solutions. Third-party backup software can leverage vStor as a target, and virtualization platforms can use it for VM backups. This openness differentiates vStor from many backup appliances that only work with paired software.
Cloud Integration: vStor 4.12 can function as a gateway to cloud storage. A vStor instance can be deployed in cloud environments as a replication target from on-premises systems. Through MinIO or DPX, vStor supports archiving to cloud providers (AWS, Azure, Wasabi) with features like S3 Object Lock for immutability.
Automation: vStor provides both a Command Line Interface (CLI) and RESTful API for automation. All web interface capabilities are mirrored in CLI commands, enabling integration with orchestration tools like Ansible or PowerShell. The REST API enables programmatic control for monitoring systems or custom portals, fitting into DevOps workflows.
Operations and Monitoring
Management Interface: vStor provides a web-based interface for configuration and operations. The dashboard summarizes pool capacities, volume statuses, and replication activity. The interface includes sections for Storage, Data Protection, and System settings, allowing administrators to quickly view system health and perform actions.
System Configuration: Day-to-day operations include managing network settings, time configuration (NTP), certificates, and system maintenance. vStor supports features like disk rescanning to detect new storage without rebooting, simplifying expansion procedures.
Health Monitoring: vStor displays alarm statuses in the UI for events like replication failures or disk errors. For proactive monitoring, administrators should track pool capacity trends and replication lag. While built-in alerting appears limited, the system can be integrated with external monitoring tools.
Support and Troubleshooting: vStor includes support bundle generation that packages logs and configurations for Catalogic support. The documentation covers common questions and best practices, such as preferring fewer large pools over many small ones to reduce fragmentation.
Conclusion
Catalogic vStor 4.12 delivers a comprehensive backup storage solution combining enterprise-grade capabilities with robust data protection. Its security features (MFA, immutability, ransomware scanning) provide protection against cyber threats, while performance optimizations ensure cost-effective long-term storage without sacrificing retrieval speeds.
vStor stands out for its flexibility and openness compared to proprietary backup appliances. It can be deployed on existing hardware and brings similar space-saving technologies while adding unique features like native object storage and ransomware detection.
Common use cases include:
- Data center backup repository for enterprise-wide backups
- Remote/branch office backup with replication to central sites
- Ransomware-resilient backup store with immutability
- Archive and cloud gateway for tiered backup storage
- Test/dev environments using snapshot capabilities
By deploying vStor, organizations modernize their data protection infrastructure transforming a standard backup repository into a smart, resilient, and scalable platform that actively contributes to overall data management strategy.


